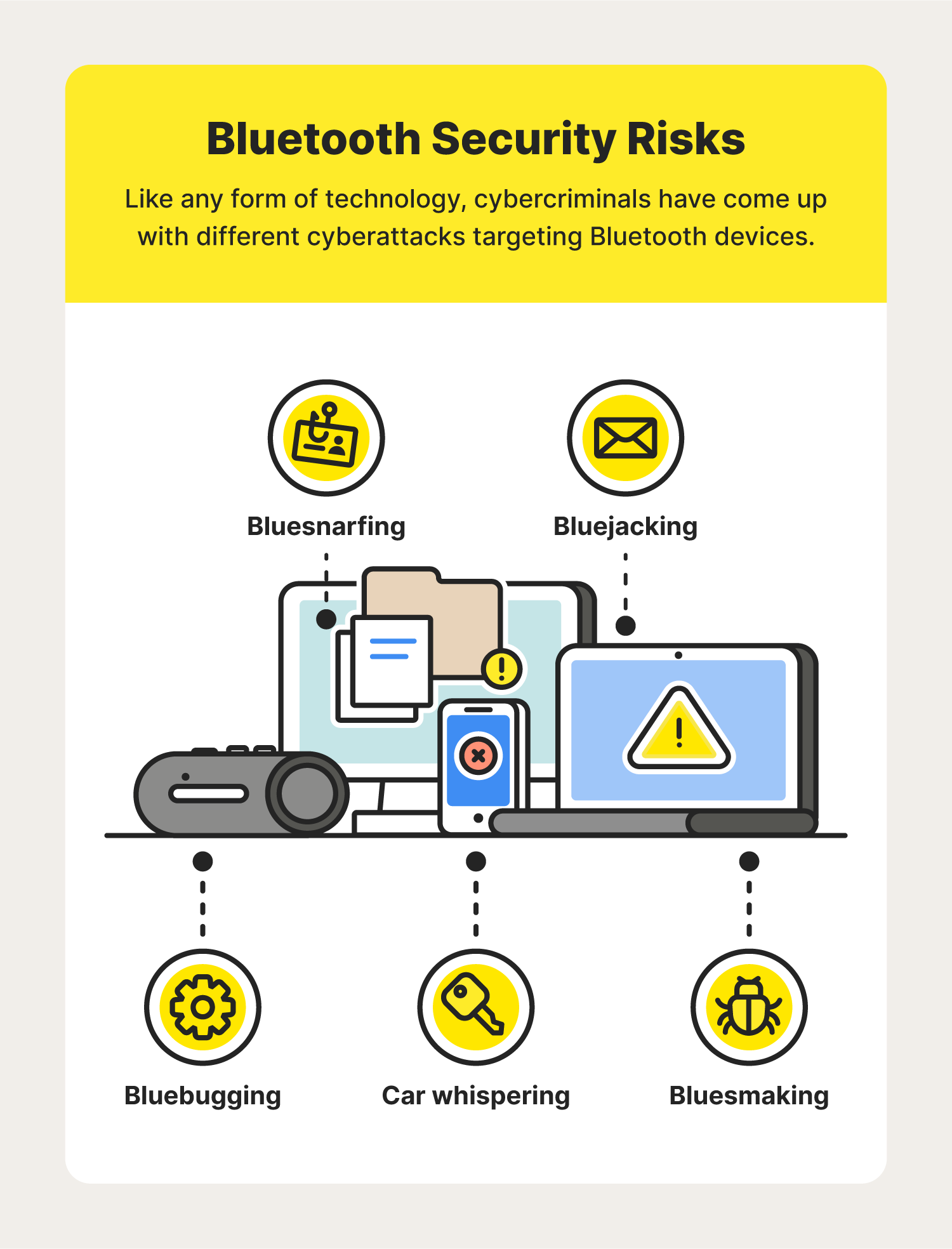
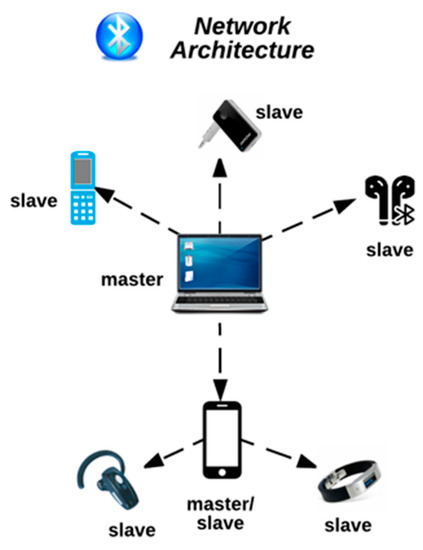
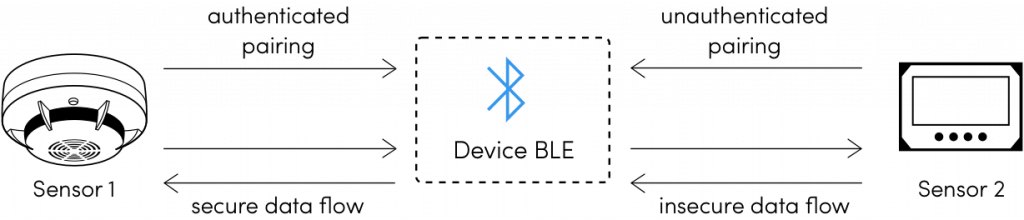
Thetis Fido BLE U2F Security Key con autenticación de Dos factores y protección Adicional Bluetooth ENBLE, Compatible con Windows/Linus/Mac OS, Gmail, Facebook, Dropbox, SalesForce, GitHub y más : Amazon.es: Informática
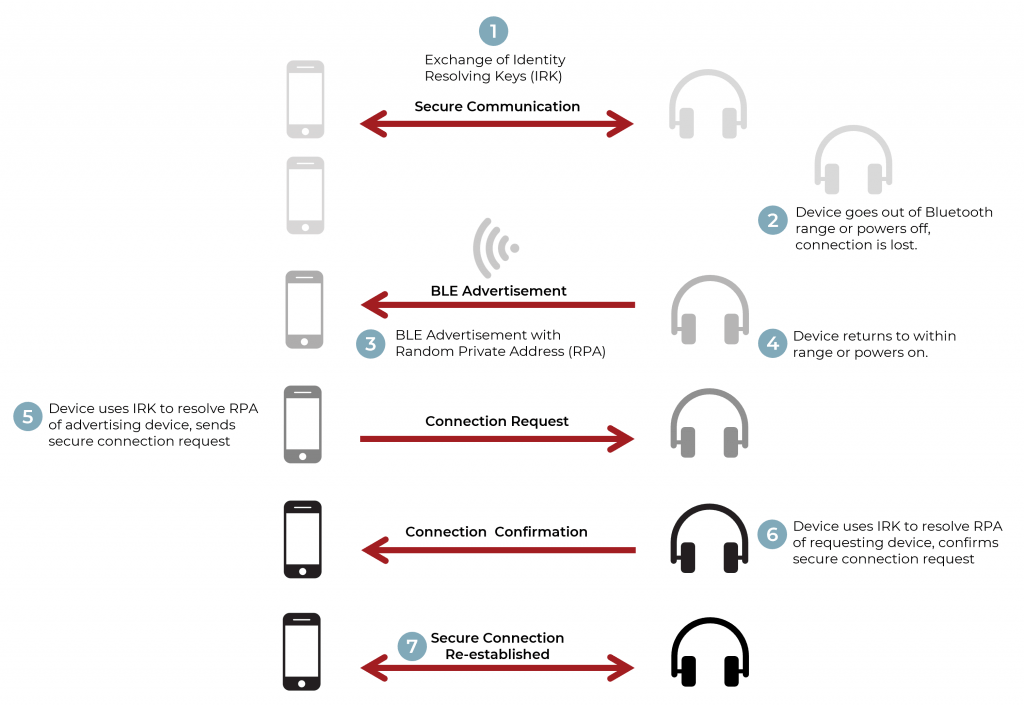
How to Implement Bluetooth Low Energy Security and Privacy in Wireless Devices - Contract Engineering, Product Design & Development Company - Cardinal Peak
How to Implement Bluetooth Low Energy Security and Privacy in Wireless Devices - Contract Engineering, Product Design & Development Company - Cardinal Peak

Guide to improve the security posture of Bluetooth Low Energy-enabled applications | by Kang Hao | CSG @ GovTech | Medium
GitHub - Charmve/BLE-Security-Attack-Defence: ✨ Purpose only! The dangers of Bluetooth Low Energy(BLE)implementations: Unveiling zero day vulnerabilities and security flaws in modern Bluetooth LE stacks.