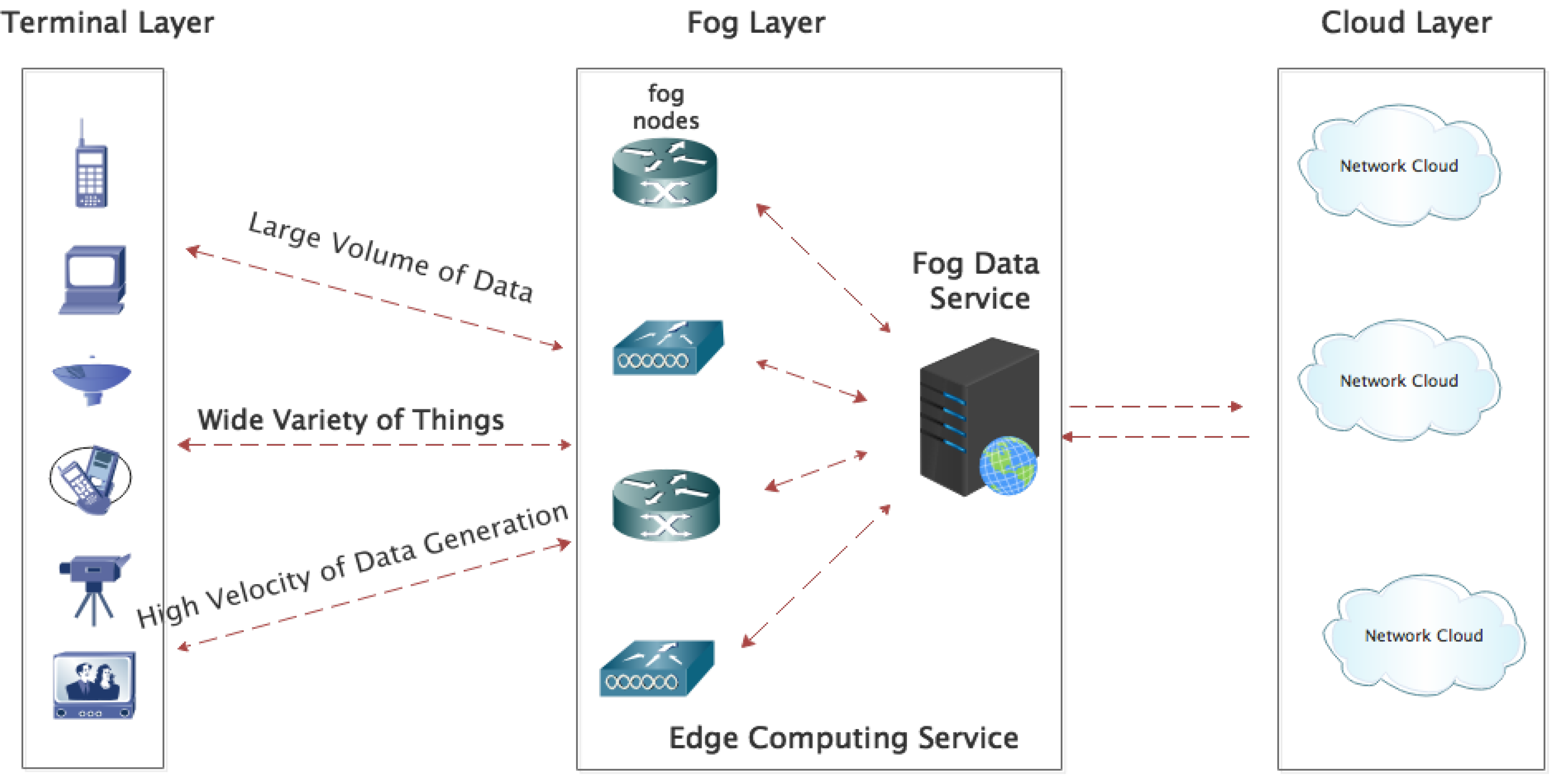
Electronics | Free Full-Text | DDoS Attack Detection in IoT-Based Networks Using Machine Learning Models: A Survey and Research Directions

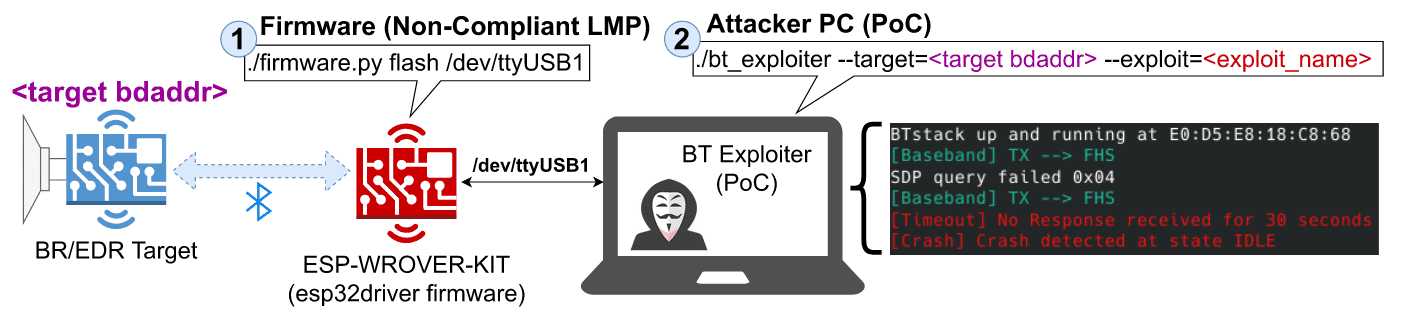
7 New Bugs in Bluetooth Let Hackers Impersonate As Legitimate Device & Launch DDoS Attacks - GBHackers - Latest Cyber Security News | Hacker News





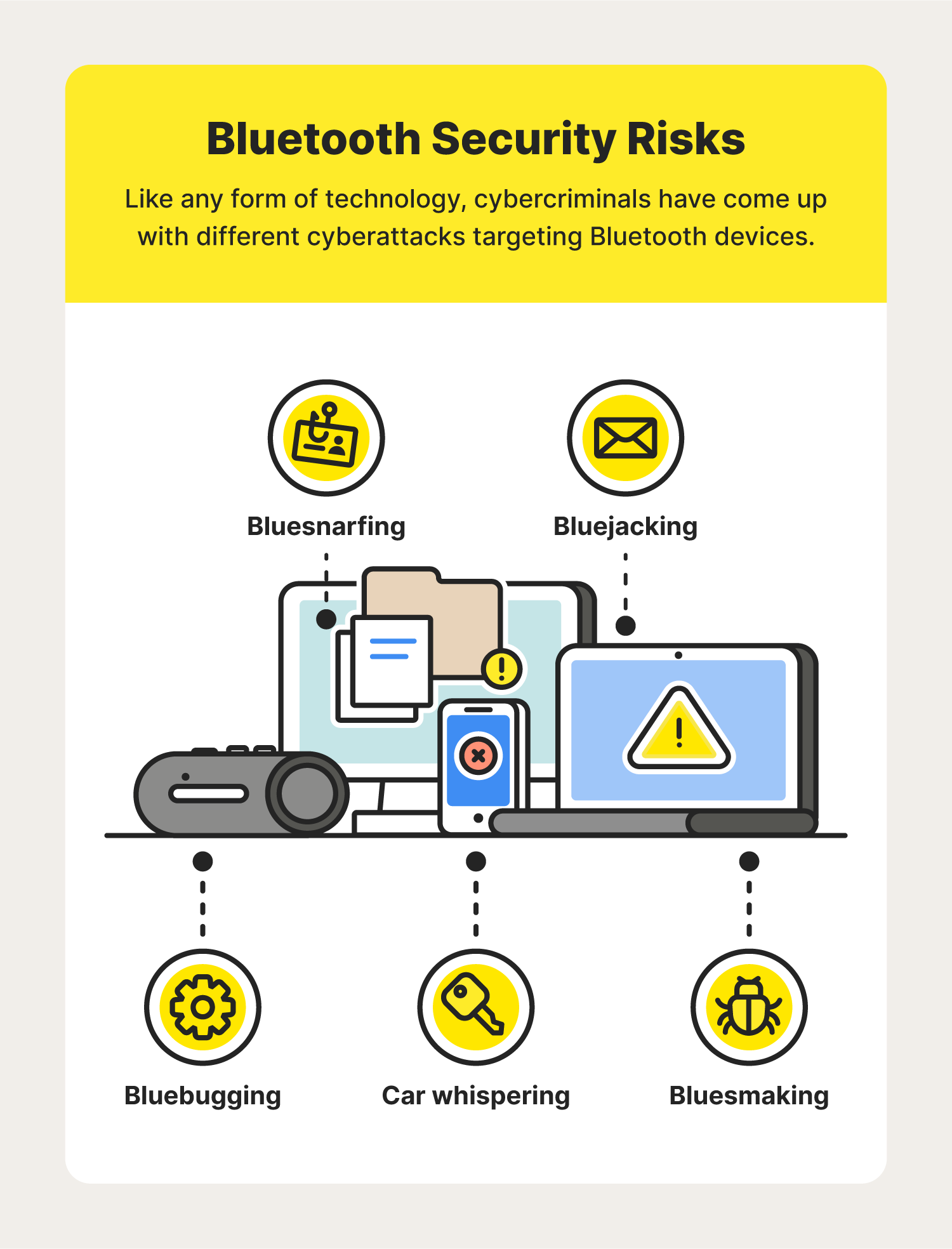



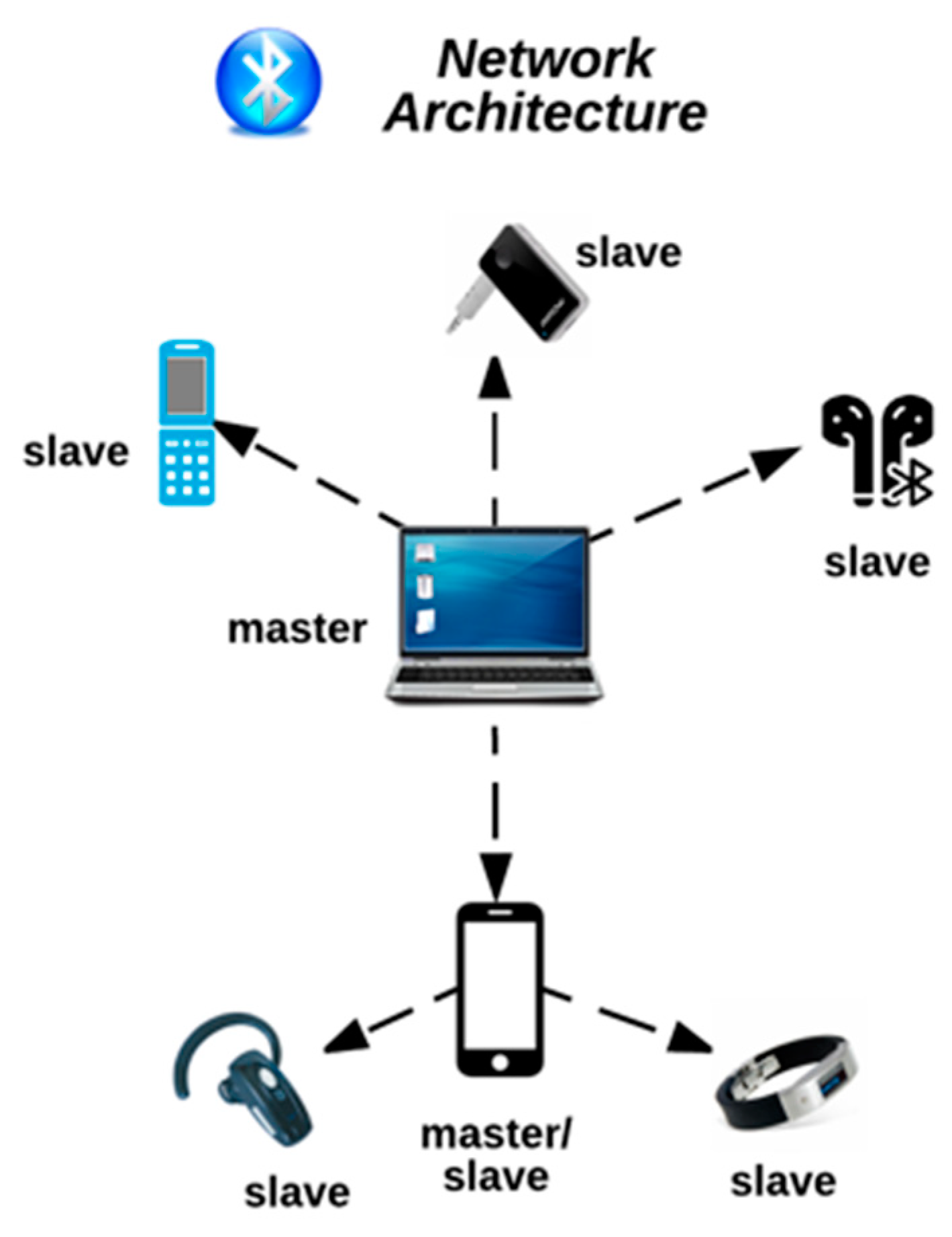
![Identify & Target Bluetooth Devices with Bettercap [Tutorial] - YouTube Identify & Target Bluetooth Devices with Bettercap [Tutorial] - YouTube](https://i.ytimg.com/vi/YDpjGTojByw/maxresdefault.jpg)